Create an intelligent system using AI/ML to detect phishing domains which imitate look and feel of genuine domains
Phishing

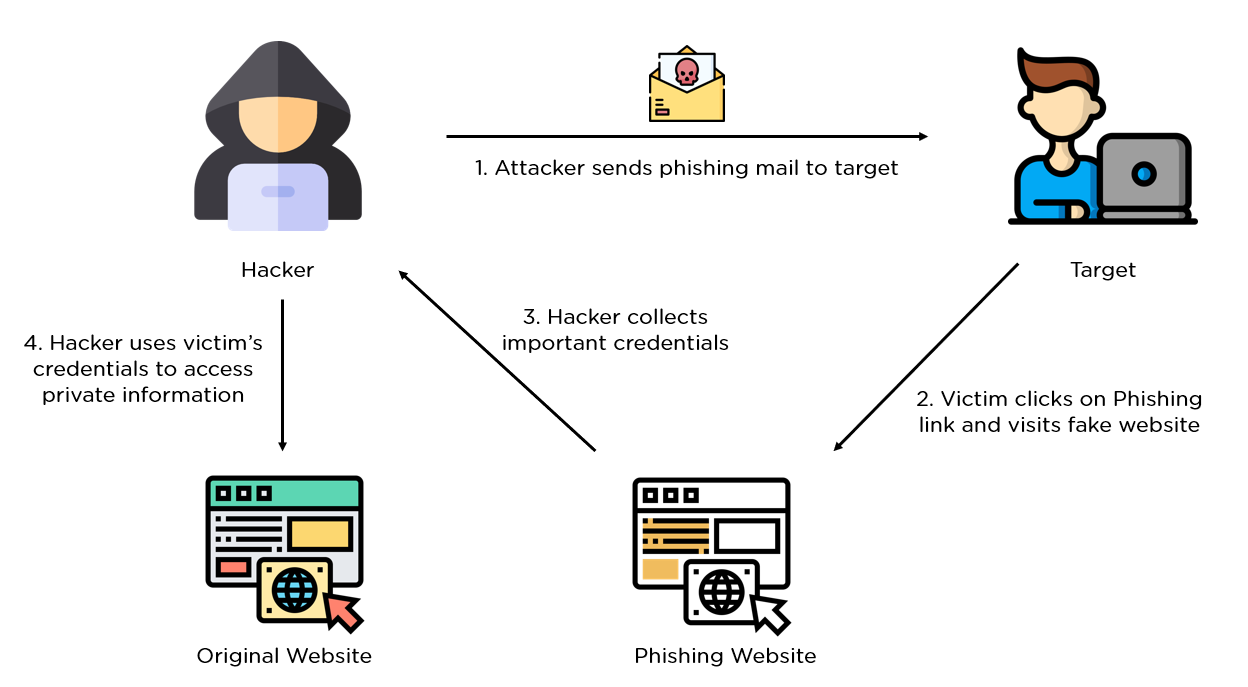
Phishing is a type of cybercrime that involves tricking people into providing sensitive information. The scammer poses as a legitimate institution and contacts the target by email, telephone,
or text message. The goal is to get the victim to visit a website that may download a virus or steal personal information.
Flow Chart :

Objective :
Creating an intelligent system to detect phishing domains that imitate genuine domains is a complex task that involves various AI and machine learning techniques.
Here's a high-level overview of the steps involved:
The steps are :
- Data Collection:
- Gather a large dataset of known phishing and legitimate domains.
Include features like domain names, registration details, SSL certificates, and webpage content..
- Feature Engineering:
- Extract relevant features from the dataset, such as domain length, subdomain count, special characters,
IP address reputation, SSL certificate issuer, and more.
- Model Selection:
- Choose machine learning models suitable for the task, such as Random Forest,
Gradient Boosting, or Deep Learning models like neural networks.
- Labeling:
- Label the dataset to indicate whether each domain is phishing or legitimate. This requires manual or supervised labeling.
- Data Preprocessing:
- Normalize and preprocess the data, handling missing values, encoding categorical features,
and splitting it into training and testing sets.
- Model Training:
- Train the selected model(s) using the labeled dataset, and tune hyperparameters for optimal performance.
- Feature Importance:
- Determine which features are most important for phishing detection. This helps in
understanding the decision-making process of the model.
- Evaluation:
- Assess the model's performance using metrics like accuracy, precision, recall,
F1-score, and ROC AUC on the test dataset.
- Model Deployment:
- Deploy the trained model as an API or service that can accept domain names as input and provide predictions.
- Real-time Scanning:
- Implement a system that continuously scans new domain registrations and web content.
When a domain is flagged as suspicious, investigate further.
- Feedback Loop:
- Continuously update and retrain the model with new data to adapt to evolving phishing techniques.
- User Feedback:
- Allow users to report phishing attempts and use this feedback to improve the system.
- Collaboration:
- Collaborate with domain registrars, internet service providers, and cybersecurity organizations to share threat intelligence.
-
Explainability:
- Implement methods to make the model's decisions more interpretable, so security professionals can understand why a domain is flagged.
- False Positive Handling:
- Minimize false positives by fine-tuning the model and incorporating feedback from users and security analysts.
--:So by this we can get control on under going phishing :--
Thank you
From Team Code
Acer
